ComBots Cup VII Combot Robot Championship, the annual world fighting championship for robots, takes place October 20 & 21, 2012 from 2 PM to 7 PM at the San Mateo Fairgrounds in San Mateo, California. The event features the “best 220-pound robots from around the world for dominance, cash, and the glory that is the ComBots Cup…” There is more information about this event at the ComBots Facebook page and at their website. Advance tickets are now available.
Coming to Kindle and Smashwords

November 2013
Oct 19, 2012
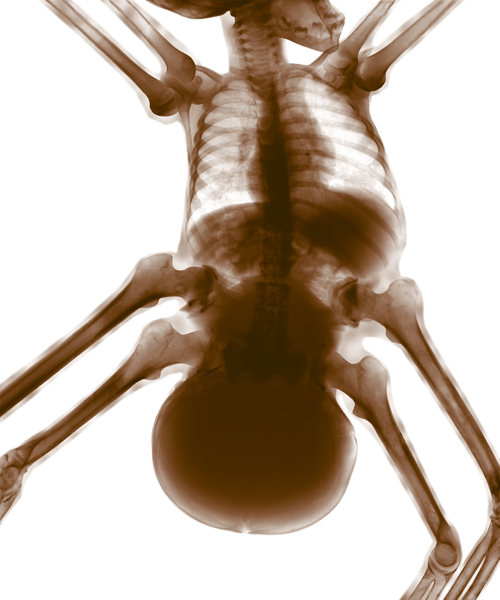
Hominid, X-Ray Style Animation of Creepy Animal/Human Hybrids
Humanoid creatures hunt one another in “Hominid,” a creepy computer animation presented in X-ray vision. The animation was written and directed by artist Brian Andrews and is based on his “Hominid” photo composite series (photos below). The animation was created at San Francisco Bay Area-based Ex’pression College for Digital Arts.
via
Researcher claims feasibility of writing lethal wireless pacemaker viruses
hope you'll make it -- tell your friends! — Cory

In a presentation at the BreakPoint security conference in Melbourne, IOActive researcher Barnaby Jack described an attack on pacemakers that could, he says, deliver lethal shocks to their owners. Jack claims that an unspecified pacemaker vendor's devices have a secret wireless back-door that can be activated by knowledgeable attackers from up to 30 feet away, and that this facility can be used to kill the victim right away, or to reprogram pacemakers to broadcast malicious firmware updates as their owners move around, which cause them to also spread the firmware, until they fail at a later time. Darren Pauli from Secure Business Intelligence quotes Jack as saying,

In a presentation at the BreakPoint security conference in Melbourne, IOActive researcher Barnaby Jack described an attack on pacemakers that could, he says, deliver lethal shocks to their owners. Jack claims that an unspecified pacemaker vendor's devices have a secret wireless back-door that can be activated by knowledgeable attackers from up to 30 feet away, and that this facility can be used to kill the victim right away, or to reprogram pacemakers to broadcast malicious firmware updates as their owners move around, which cause them to also spread the firmware, until they fail at a later time. Darren Pauli from Secure Business Intelligence quotes Jack as saying,
“The worst case scenario that I can think of, which is 100 percent possible with these devices, would be to load a compromised firmware update onto a programmer and … the compromised programmer would then infect the next pacemaker or ICD and then each would subsequently infect all others in range,” Jack said. He was developing a graphical adminstration platform dubbed “Electric Feel” which could scan for medical devices in range and with no more than a right-click, could enable shocking of the device, and reading and writing firmware and patient data. “With a max voltage of 830 volts, it's not hard to see why this is a fairly deadly feature. Not only could you induce cardiac arrest, but you could continually recharge the device and deliver shocks on loop," he said.Manufacturers of implanted devices have been resistant to calls to publish their sourcecode and to allow device owners to inspect and modify that code, citing security concerns should latent vulnerabilities be exposed, and put implantees at risk. But as Jack's presentation demonstrates, vulnerabilities can be discovered without publication -- and if they are discovered and not disclosed, they may never be patched (or may not be patched until coming to light in some kind of horrific attack). In other words, secrecy helps bad guys, but keeps good guys and innocent bystanders in the dark
Subscribe to:
Comments (Atom)